CSAW 2017 - DNE
About DNE:
Our name expanded to Does Not Exist is also an acronym for the names of the members in our group. We are fourth year students in JCT's computer department.
We are also the first group to complete all the challenges for the CSAW 2017 event. Hurrah!
Cryptography (1100)
Find the missing value - 100
Challenge:
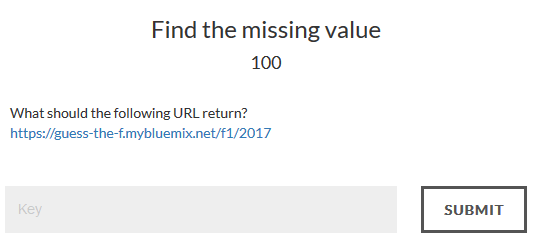
The website:
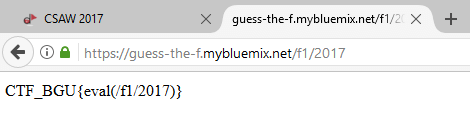
We realized we need to figure out what the computation for 2017 is.
We tried to understand what different numbers gave us so we changed the 2017 to 0, 1, and -1. The values we got were -1, 7, and 7 respectively. We tried a few more numbers with their negatives and realized they were always the same, so we put -2017 which gave us 4309384346854701617671.
Success!
---- Here Come Dots ---- - 200
Challenge:
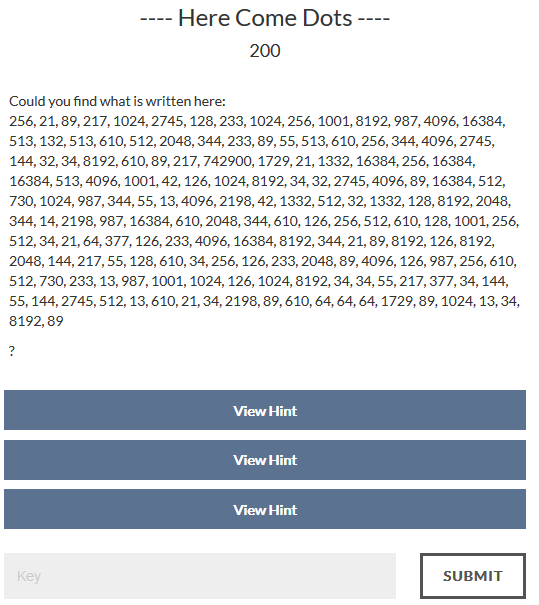
The hints were beyond useless, I won't even bother putting them here they were so bad.
After a long time of trying to find all sorts of patterns we noticed we could separate these numbers into three groups: Powers of two, members of the Fibonacci Series and everything else. So, we wrote a python script that converts each of these numbers into a ., - or and converted the resulting Morse code into text.
original_list = [256, 21, 89, 217, 1024, 2745, 128, 233, 1024, 256, 1001, 8192, 987, 4096, 16384, 513, 132, 513, 610, 512, 2048, 344, 233, 89, 55, 513, 610, 256, 344, 4096, 2745, 144, 32, 34, 8192, 610, 89, 217, 742900, 1729, 21, 1332, 16384, 256, 16384, 16384, 513, 4096, 1001, 42, 126, 1024, 8192, 34, 32, 2745, 4096, 89, 16384, 512, 730, 1024, 987, 344, 55, 13, 4096, 2198, 42, 1332, 512, 32, 1332, 128, 8192, 2048, 344, 14, 2198, 987, 16384, 610, 2048, 344, 610, 126, 256, 512, 610, 128, 1001, 256, 512, 34, 21, 64, 377, 126, 233, 4096, 16384, 8192, 344, 21, 89, 8192, 126, 8192, 2048, 144, 217, 55, 128, 610, 34, 256, 126, 233, 2048, 89, 4096, 126, 987, 256, 610, 512, 730, 233, 13, 987, 1001, 1024, 126, 1024, 8192, 34, 34, 55, 217, 377, 34, 144, 55, 144, 2745, 512, 13, 610, 21, 34, 2198, 89, 610, 64, 64, 64, 1729, 89, 1024, 13, 34, 8192, 89]
power_list = []
for i in range(20):
power_list.append(2**i)
fibonacci_list = [1,1]
a = 1
b = 1
for i in range(20):
c = a+b
fibonacci_list.append(c)
a=b
b=c
ans1 = ""
ans2 = ""
for i in original_list:
if i in power_list:
ans1 += "."
ans2 += "-"
elif i in fibonacci_list:
ans1 += "-"
ans2 += "."
else:
ans1 += " "
ans2 += " "
print(ans1) # .-- . .-.. .-.. -.. --- -. . -.-.-- - .... . ..-. .-.. .- --. .. ... -.-. - ..-. ..--.- -... --. ..- -.--. -.-. -.-. --- . ..--- ----- .---- --... -.--.-
# welldonetheflagisctf_bgu(ccoe2017
print(ans2) # -.. - -.-- -.-- .-- ... .- - .-.-.. . ---- - --.- -.-- -. ..- -- --- .-.- . --.- --..-. .--- ..- --. .-..- .-.- .-.- ... - --... ..... -.... ..--- .-..-.
# dtyywsatetqynumoäeqjugèääst7562" The correct option was ans1 which gave: welldonetheflagisctf_bgu(ccoe2017.
Success!
Find the missing value II - 300
Challenge:
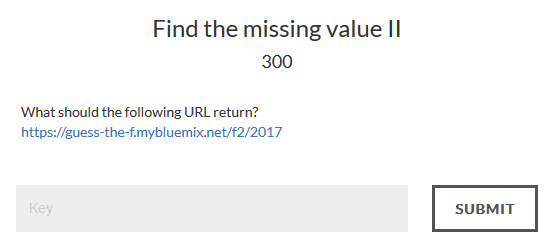
The website:
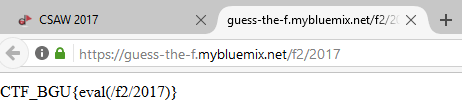
Similar concept as the first one.
This time we got long strings comprised solely of ints, so, we tried converting to hex to see maybe there was something there. It turned out the result was the md5 hash of the input surrounded by quotation marks. So, we calculated the hash of "2017" and converted the result to its decimal representation.
Success!
Find the missing value III - 500
Challenge:
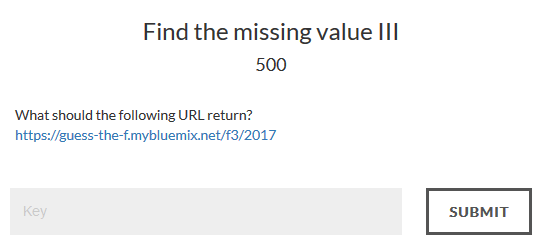
The website:
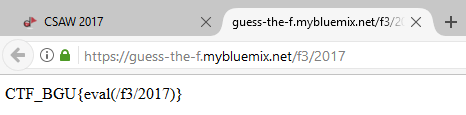
Again, the same idea.
This time we noticed the values looked kind of like md5 hashes, luckily Google is amazing and returned that hash for 1 (e4a7afdacb8b63d1de55011d2202c77e) is the hash of "7" and so on for all the other results we were supposed to get from the first challenge. So, we wrapped the flag from one with " and hashed it.
Success!
Machine Learning (900)
Spam classifying - 100+300+500
Challenge:
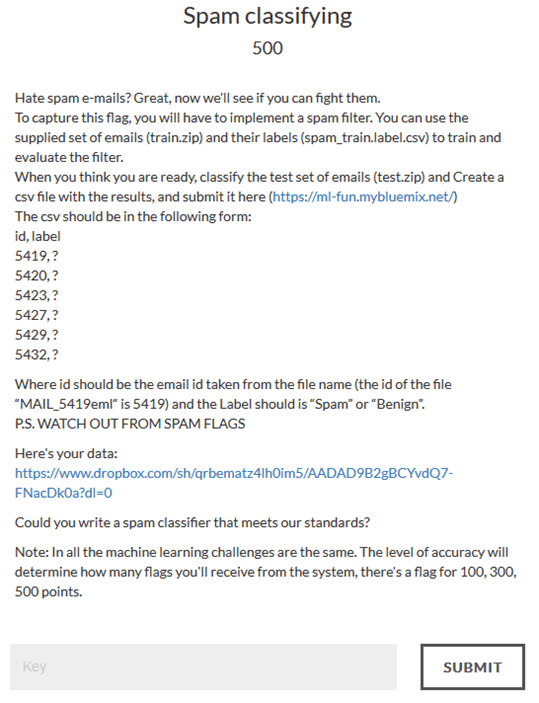
Pretty standard machine learning stuff. We uploaded our result and got all three flags. (That sentence is pretty meaningless, but the solver didn't bother giving more info so...)
Success!
Reverse Engineering (600)
Can you run this code? - 100
Challenge:
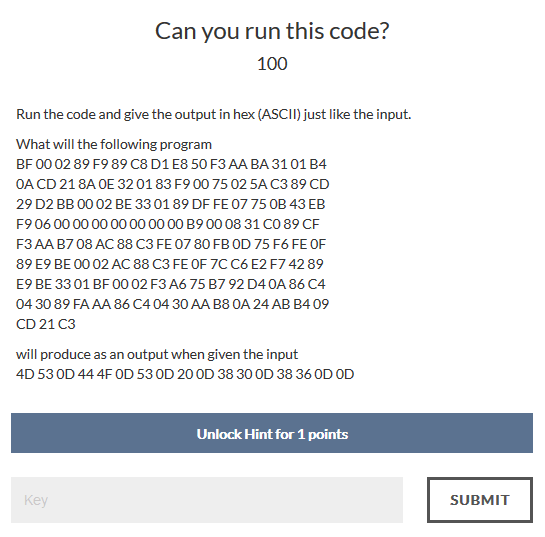
This is actually 8086 machine code, we ran it on a dos simulator and got the result.
Success!
Can you run this code? #Harder - 500
Challenge:
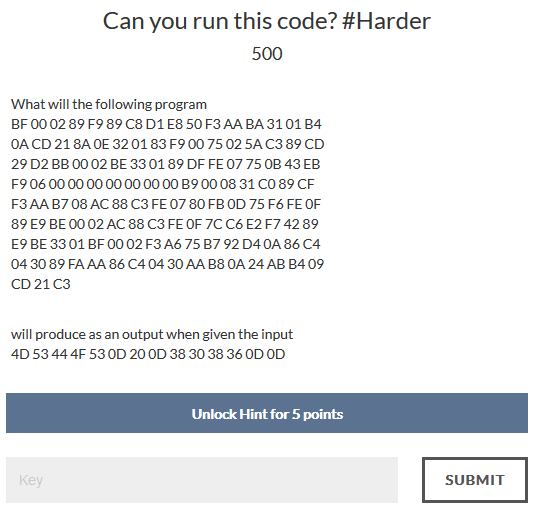
This is actually the same code as the previous challenge, but the input is longer so it takes more time. The dos emulator we were using was so slow we decided to boot FreeDos from usb and run the code on that. After a few hours...
Success!
Web (900)
Fraud Transactions - 100
Challenge:
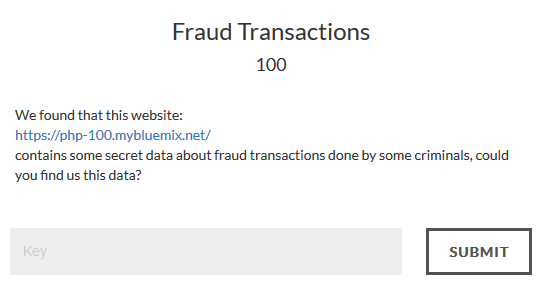
The website:

Logged in as admin with the password admin ('cause that's not the point of this challenge) and got this page:

Of course, we hit the big red button that said, Show me the file! but alas:
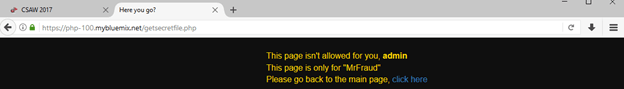
But how do they know which user I am? Cookies!
Obviously identifying a user by the base64 representation and the sha1 hash of their username in cookies is smart. We calculated the correct values for MrFraud and boom.
Success!
Hack my Account - 300
Challenge:
The website:
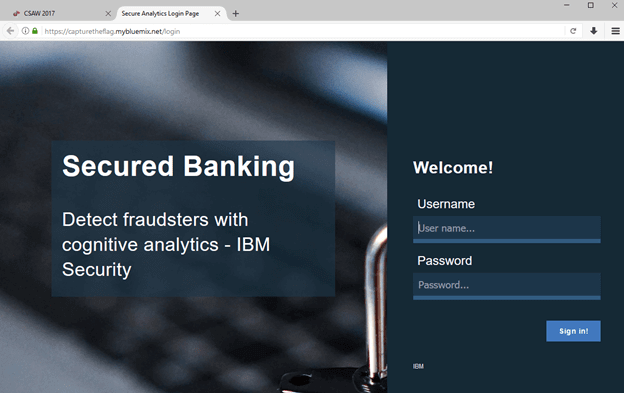
The username and password were actually in plain text in the JavaScript running this site. The only problem was that you couldn't copy, paste, erase, press tab and only had a few seconds to input the information. I guess it's good I type quickly.
Success!
Could you log as admin? - 500
Challenge:
The website:
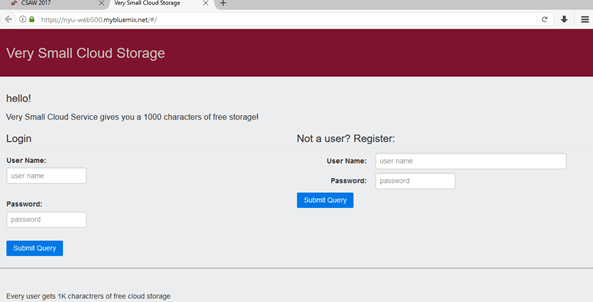
At first, we thought we needed to do some sort of AngularJS injection, but we noticed a certain cookie that changed only according to a parameter sent while trying to login called log_sequence. There was also a timer that let you stay on the site for 120 seconds; every time the timer ran out the log_sequence went back down to one. After plenty of tries we finally got a cookie for that log_sequence. The site used two cookies to determine who a user was, we described the first one. The second cookie was the md5 hash of the username. So, we took the md5 hash of admin and the other cookie we found, waited for the timer to end and then tried to log in with the fake cookies.
Success!
Forensics (650)
e-sumo - 100
Challenge:
The pcap contained some sort of capture of mouse movement. Using a custom graphics library written by Internal Error ⚠️ we managed to recreate the drawing which contained the flag.
Success!
Missing bytes - 250
Challenge:
Using HexEdit and Google we came to the conclusion that this was a "MIDI" file that gave us the first 4 bytes 4D 54 68 64(=MThd). We then had to understand how "MIDI" files are structured and fix the challenge file so that we could play it. We had to erase an extra byte from the end, add "footer" bytes (00 FF 2F 00) and change the byte that said how big the file was. After doing all this we could play the song, which turned out to be "Mary Had a Little Lamb". It was missing the last two notes however, ughh, but at least we know what to add. After a long and hard battle, we finally managed to find the correct representation of the missing bytes, restore the file size marker and complete the file. We took the 4 bytes from the header and the last 16 bytes from the file and that was the key.
Success!
Here the password -300
Challenge:
This pcap had a telnet communication log that contained base64 representations of two files as.wav and items.zip. There was another audio file hidden in the hex of the zip file. After being reversed and slowed down we could hear that it said iamdavej which was the password for the zip. The zip contained a csv file that seemed to hold just a random list of items and numbers.
Salt,1334
Milk,2069
Butter,2619
Mushrooms,3347
Carrots,3857
Peanut Butter,4697
Cookies,5597
Potatoes (Organic),6426
Tomato Sauce,7196
Eggs,7901
Rice,8684
Chicken (Fresh),9570
Olive Oil,10370
Soymilk,11014
Granola Bars,11896
Apple (Organic),12737
Hummus,13354
Pizza (Frozen),14013
Frozen Blueberries,14571
Cheese,15120
Bread (Sliced),15952But we still had an as.wav file that we didn't use, so we tried to extract the bytes corresponding to the numbers, and what do you know?
Success!

