Cyber Week 2017 - JC[ider]T
Challenge 1:
We got a download link for a pcap file.
Right as we opened the pcap we saw an image was sent key.jpg, we assumed some sort of steganography. Luckily it was simple, another file was placed after the end of the image. We extracted the file which was a GZip file and extracted its contents. Hurray a private key.
We configured Wireshark to use the key and decrypt our data.
Now we saw a couple new files: mystery.docx and FLAG.txt.
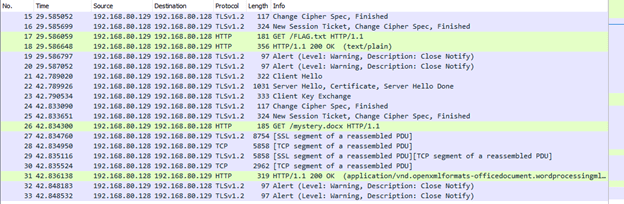
The text file contained the key for the first challenge. First flag is: e-OrhJKccg!VJ&Ng0.
Challenge 2:
The docx file was password protected. In order to use john the ripper to crack the password we first had to get its hash. Using office2john.py we exported the hash to a new file mystery.hash.
$ ./office2john.py mystery.docx > mystery.hashThen using john the ripper, we found the password lucky1.
We opened the docx file using the password we got and saw this:
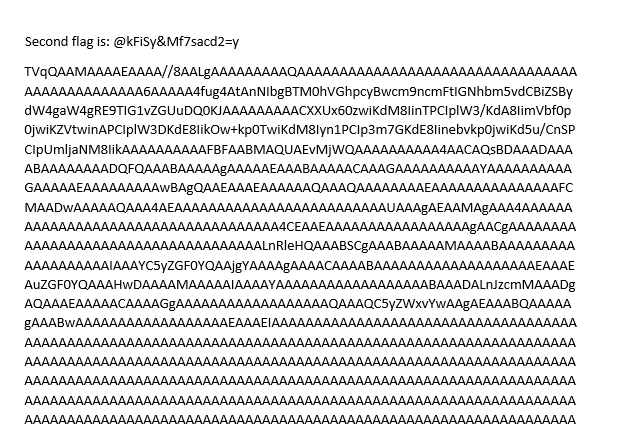
Yay second challenge done!
Challenge 3:
It looked like all that strange text is important so we copied it to a new file.
We had no idea what is was, but in doubt try base64!
Yay seems like it worked!
We saved the file as an exe and tried to run it (safe, right?).
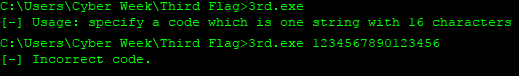
So… IDA!
As we already know from running the program we must input a string that is 16 characters long, now we need to find out what that string is. If we run the program with a debugger in IDA we can see that it compares the result of a calculation on our input with a predefined password, let’s call this compKey.
We also saw that it goes over the password in 4 pieces and does a XOR command between the part and some sort of key. Specifically, it takes the first 4 characters of the input and XORs them with a saved string Z$9n and saves that in some sort of resArray. Next it takes the result and XORs it with the next 4 bytes of the input and so on. [Side note: If we do XOR twice then it’s like not doing XOR at all.] We divided compKey into 4 groups:
- compKey1=
\x10\x46\x79\x20 - compKey2=
\x52\x10\x4F\x7F - compKey3=
\x3F\x63\x09\x4B - compKey4=
\x0F\x36\x3D\x13
We know how they check the password and we know how XOR behaves so now we can use that to find the password. We XORed that with compKey1 and got “Jb@N” which is the first part of the password, good we’re on the right track. Next, we XORed compKey1 with compKey2 and got BV6\_. Then compKey2 with compKey3 and got msF4 and finally compKey3 with compKey4 and got 0U4X.
We combined them all into a new string Jb@NBV6\_msF40U4X.
C:Fake Path>3rd.exe Jb@NBV6\_msF40U4X
[+] Third flag is: %Tk9Y@(*=T94z)9SkYay! All done.

