Mossad Challenge - 5776
Introduction:
A picture was posted in "Israel HaYom" newspaper on Yom Hazikaron [2016] by Mossad:

On the right side of the image it says "ARE YOU READY FOR A CHALLENGE?" and in between those words it says "IP". Based on the selected text we can assume the selected hex digits are the ones that make the ip we are looking for.
Challenge 1:
Using a calculator we got (82)16=(130)10 (d3)16=(211)10 (54)16=(84)10 (aa)16=(170)10. We entered the ip (130.211.84.170) into a browser and got this page:
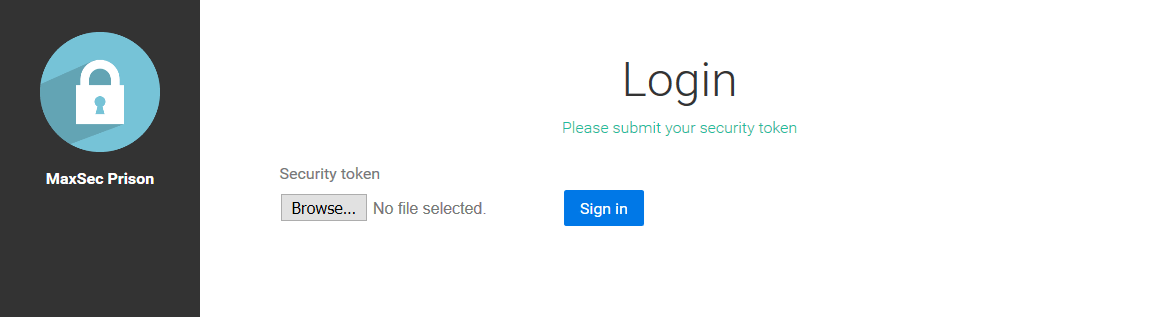
Clicking on "Start Challenge" brought us to this page:
Uploading a few files helped us find out we were looking for a .png image with a particular xmodem-crc and within a certain size range, so we tried to find what that image was.
We were able to open the image that was on the left side of the page and investigate its URL: http://130.211.84.170/challenge1/get-image?name=logo.png&h=87d41d15f&multiple=0
After some trial and error we found that the "h" in the URL was the [3]-[11] spots in the md5 hash of the file name (characters 4-12). We also wondered what the "multiple" parameter is, after playing around with it we see that when it has the value 1 we get a list of the file name: ["logo.png"]. Taking all this into account we tried to see if maybe there are other files on the server, so we hashed \* and took the 9 digits discussed earlier (9dae361af) and put these values in the URL: http://130.211.84.170/challenge1/get-image?name=*&h=9dae361af&multiple=1.
This is what we got ["last-login.png", "map.png", "themissingpiece.png", "logo.png", "a.jpg", "fingerprint.jpg"].
We opened all the images:
 |
 |
 |
 |
 |
 |
|---|---|---|---|---|---|
| 1last-login.png | 2map.png | 3themissingpiece.png | 4logo.png | 5a.jpg | 6fingerprint.jpg |
After attempting to upload all of them we found that the only one that has the correct crc is "last-login.png":
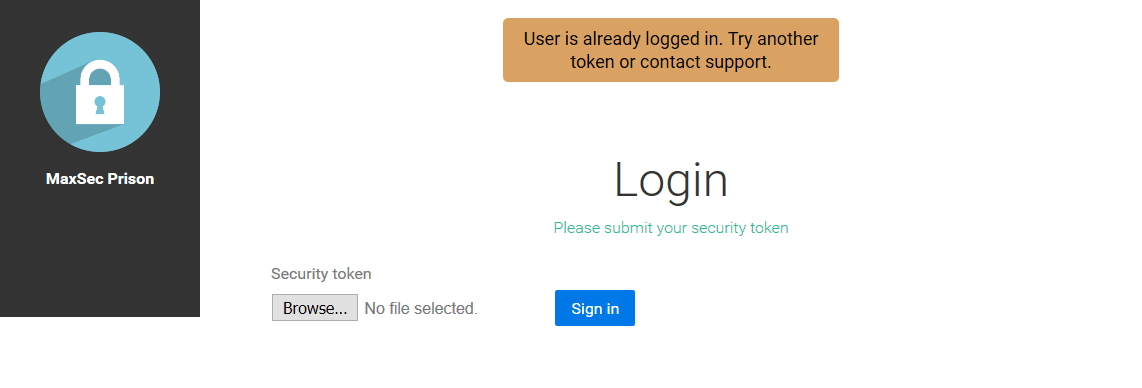
We gathered from this that we need to upload a different image with the same crc. After some research we discovered that crcs can be easily manipulated by adding 4 bytes to the file and monitoring the affect they have. We wrote a script that helped us do that and got a new image that lets us login.
As we can see more options became available in the menu. Going through them we found that we have access to the "Cells" and "Door Control" pages.
In the "Door Control" page we got what appears to be a code in base64:
UEsDBBQAAAAIAFxYs0jX0N92qAMAAAAKAAAPAAAARG9vckNvbnRyb2wuZXhl842awMDMwMDAAsT//zMw7GCAAAcGwuAAEPPJ7+Jj2MJ5VnEHo89ZxZCMzGKFgqL89KLEXIXkxLy8/BKFpFSFotI8hcw8BRf/YIXc/JRUPV5eLhWoGTsrlQ/+lfCdBMMKz9sm/QOzfSb9ANINiWsn/QHTk8F0UGZyBkgdzA0BrgwMPozMDPxr7oXBxB4wMDFyM/IwMDBBPQYCAlCsAPUdiA2UZ4NKw2iwx6F6mBkcWsEKBaAGCCCMgoE/QPM08AWSAQODDBFhiQGA5krgkdYrSa0oAdITGBngfoH7FWFEgl5RSmJJIgPDFEaIAFgdG6o6ByDSK0rNyU+GutUAqo4DQ50TOV4ZBYMXhHa/aXxjAEwcwWHhWayR+yQUHBh6ax98XrpPB8w6k6UaaXy7tzXz////S7OSgwOWdszNALGXLtnnAFKx98K///8/L01buuSFBNCY5iM83YcbSlgf3HBo/iFc8zU4OIs5ONj4W6/vA7ewwP+iDEA9zT/+87c8Aloe3Ov7IzBLsLcXZGJgwH9RFqBs6wH+lqNAyebaHwL8rbuBrO7TXS68Z6xaeEHK+FtXAIUcm38KFL3s/tywxRRk/6oSTrfGf9OBEkVvu20FQO5y/RIckCWccQPIzvr6/3q3LA+QFfD/chZQ6kdAFnOv65+ArG//rwNt5QDbWspqfMDhdQDQWubSrw21f4xK3zfU/rUofdnl+k/HwIaz/AFI65eALN6MN1BDgcY11P4zLBWFyIT1toIcEwCVMj7wmqn7WHxcdPfT2MPAcO725eFf7yvQerJEtPui8YHw7lqOgy+ZPq/uPtX8kPnzqvhuV47Yw/SOfx9FBoYoIE4D4jIgtlGEiO9+1LJn+/ZVq1t2b9+2b+P+b2sWrGFItorxL0jNc8nPLyrWy06tBKk7dO/erQmtrbNnzmqZMXt2y6R5LbPnzmo9eej0sWPnj5w9P7v15v2TJ8/fvNk6e/65WXNOzLz/9fS8+3OPH7w/t33urWft84H4wuQb99vvPDs+6c7c9sl3Tsw4ePPG8+mrdlMCGBhc80pSixSSU3NyFPJKc5NSi6wUGEAOVwD5IDWFiwvodhVFRDi0gdgKpIXRASb31JLgkhSPxLyUnFQGhl0MzkWpiSWpbpk5qY4MASxBqYkpIDYDgwuY7ZyfV5wPkmK4xhpelFmSChfwdg3yc/UxNtJLycmhWVRjBwKQMl/AQMrAxqDAoM/gisEDg1cGLIamhnR2ySgYAAAAUEsBAhQDFAAAAAgAXFizSNfQ33aoAwAAAAoAAA8AAAAAAAAAAAAAAIABAAAAAERvb3JDb250cm9sLmV4ZVBLBQYAAAAAAQABAD0AAADVAwAAAAA=Using an online decoder we got what appeared to be some sort of file, the file header PK told us it was a zip file so we saved the decoded text with that extension. Extracting the zip gave us DoorControl.exe that at first seemed to do nothing at all. Running It through OLLYDBG we discovered it was looking for a file: C:\\doors\\config.txt and there were also hints the content of the file needed to be c:\\OpenDoors.key. We created this file and ran the exe, this time it requested an input which we got from the "Cells" page:
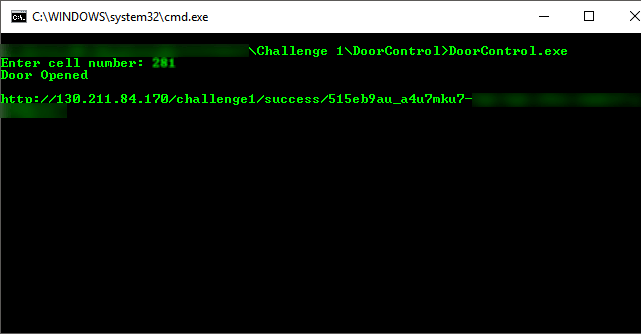
Entering the URL we got from the exe we arrived at this page (YAY!):
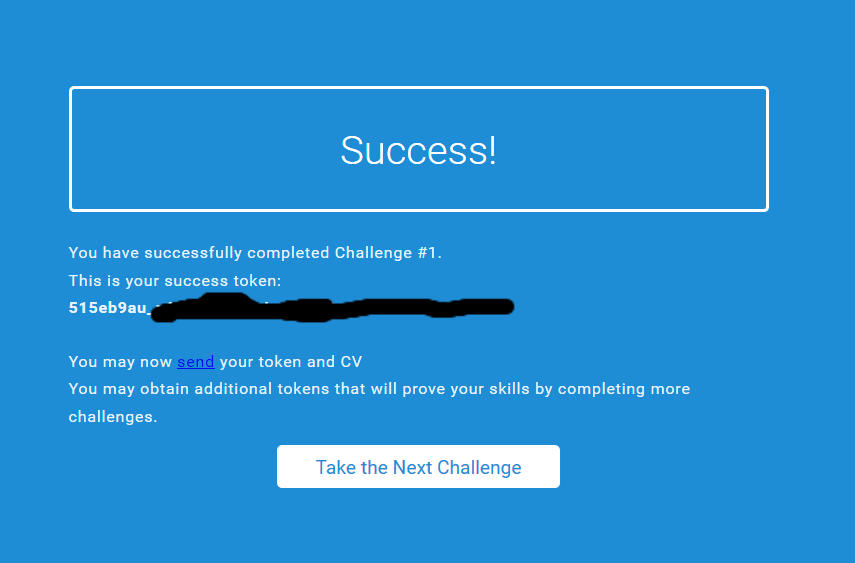
Turns out the "multiple" parameter was just a time waster, gg Mossad.
Challenge 2:
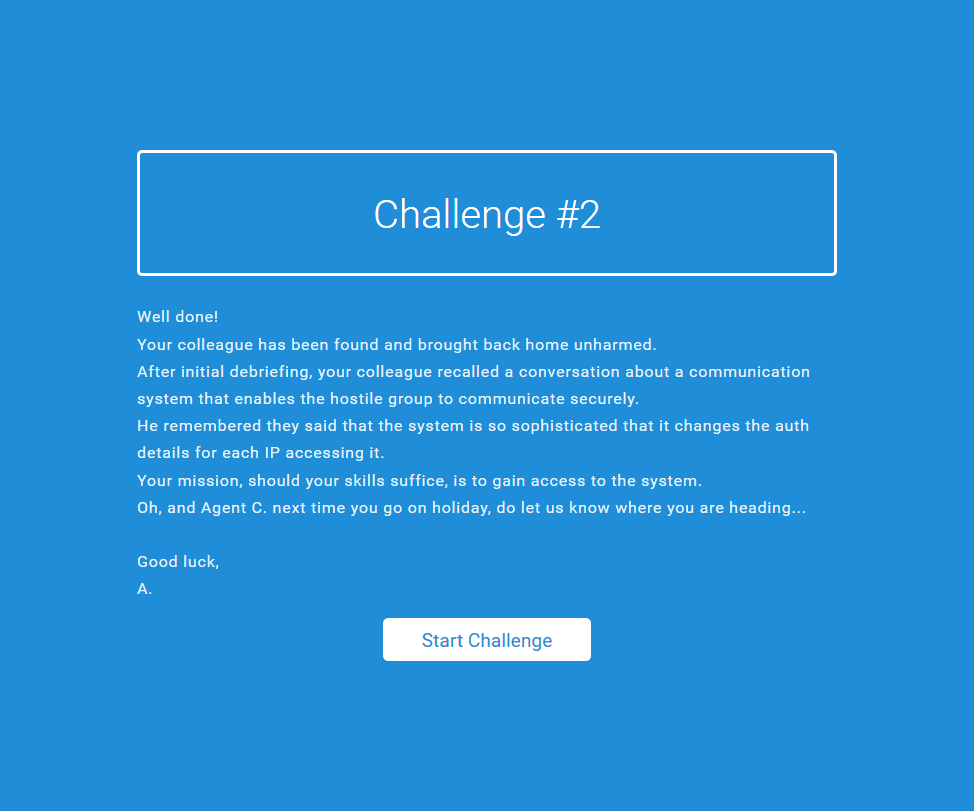
Upon clicking Start Challenge we got redirected to http://130.211.84.170/challenge2/access-denied.
Using Wireshark we discovered that there was a commented out URL in the network packet http://130.211.84.170/challenge2/pk. This downloaded x.zip inside that we found 2 files port\_knocking.cfg and random.
port\_knocking.cfg contained a list of ports to knock on and a destination port. After accessing the remote server we found some files most of which were useless. The most interesting one is login.exe. Running the exe we get a message box containing a URL:
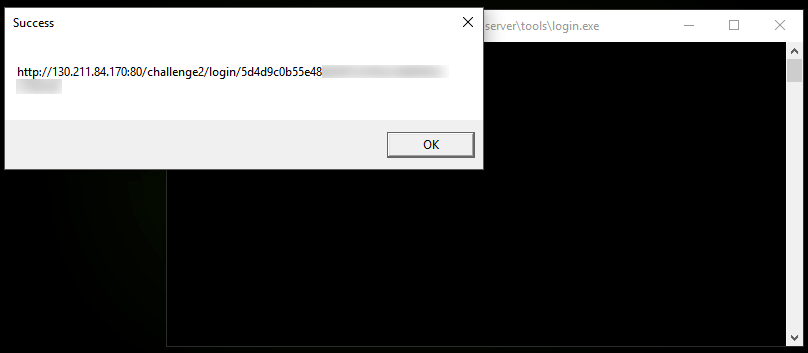
We get to a page containing two almost identical bitmaps:
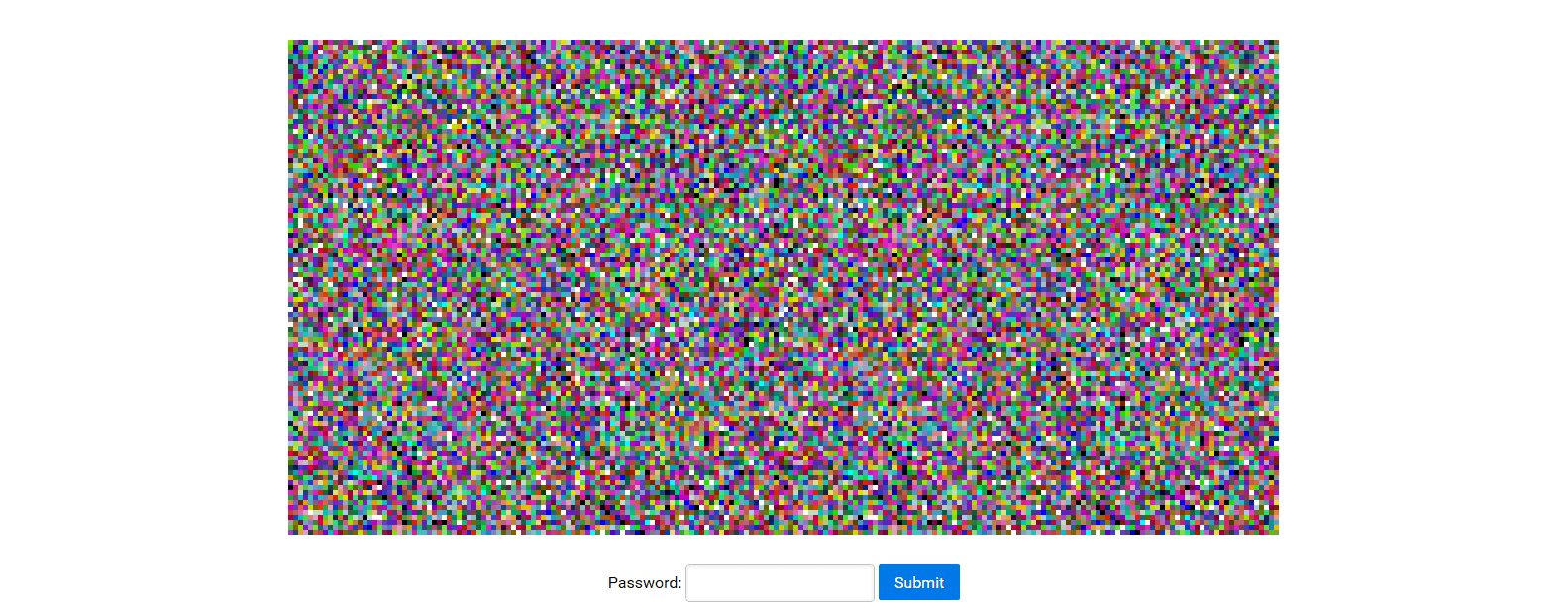
We compared the images and found the correct password (Yay again):
And here "random" was irrelevant (well so were most of the files on the server). Also I can only assume that Mossad messed up with the zip because newer versions had no problem unzipping the file whereas old versions unzipped a different text file that said "Not that easy…" (or something to that affect). Maybe the lessen is to keep your software up to date…
Challenge 3:
Hopefully more will be added soon. (guess not RIP)
"Start Challenge" brings us to 130.211.84.170/challenge3/start where there is a message: Transmitting to your.ip:XXXXX and a 5 second counter. "your.ip" is the ip of the device you're using and "XXXXX" is a random port that changes on every refresh. I guess we were supposed to do some sort of port forwarding but we didn't have that kind of access rights where we were working on this.
Sadly the challenge has ended (19/05/2016), maybe next time.