Mossad Challenge - 5777
Introduction:
A picture was posted in "Israel HaYom" newspaper on Yom Hazikaron [2017] by Mossad:
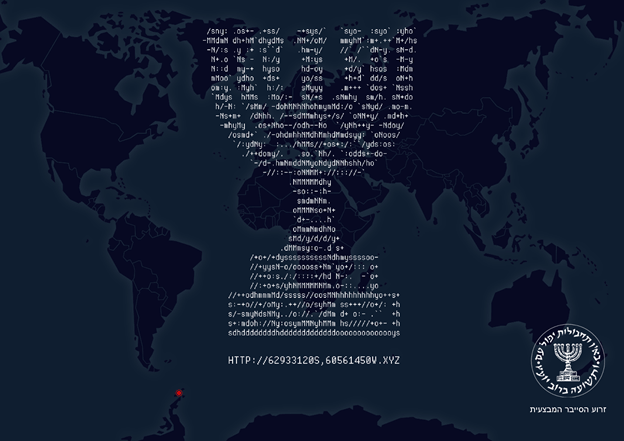
At the bottom of the image we see what appears to be a URL HTTP://62933120S,60561450W.XYZ, clearly this is not the actual URL. Let's go down the rabbit hole.
Challenge 1:
62933120S,60561450w looks a lot like coordinates so after adding appropriate dots 62.933120S,60.561450w google returned a small island off Antarctica called Deception Island. replacing the coordinates with that name we get http://deceptionisland.xyz/ success!

Clicking the link brings us to this page:
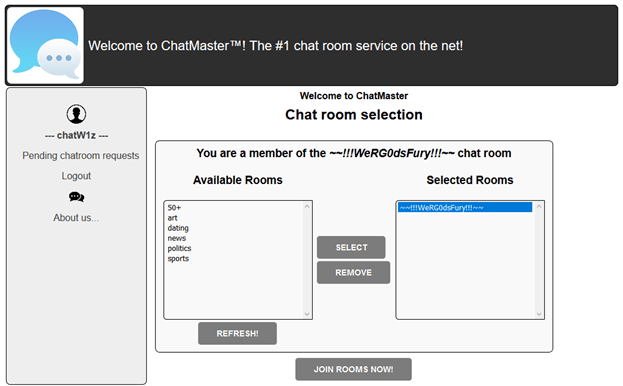
Registering brought us to the end of a waiting list. For some reason there was a cookie with our username in base64. We changed the cookie to show a different user and pressed De-register. It worked. We repeated this for all the users. After removing all the other users we managed to log in.
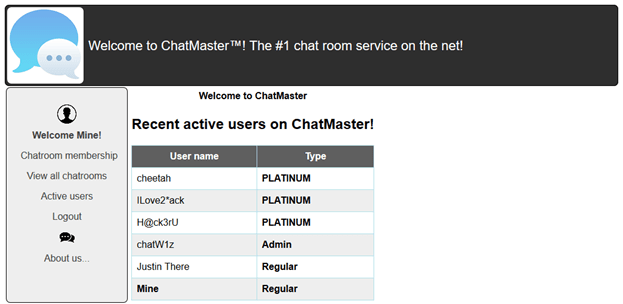
We tried to get the hint for an admin user:
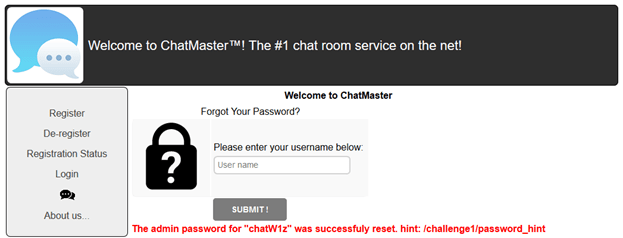
Navigating to that URL gave us a zip file password\_hint.zip that was locked with a password. Short brute force revealed that the password was doc1. The zip contained PassMasterExtension3\_1.dll.
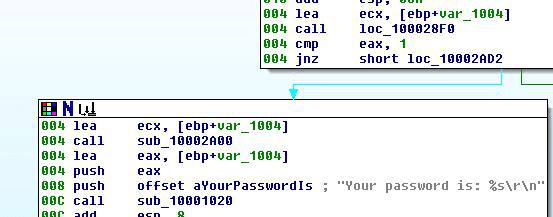
To get the dll to print a password we had to manipulate the code in such a way that it skipped a jump.
We used the password we got to log into the admin account.
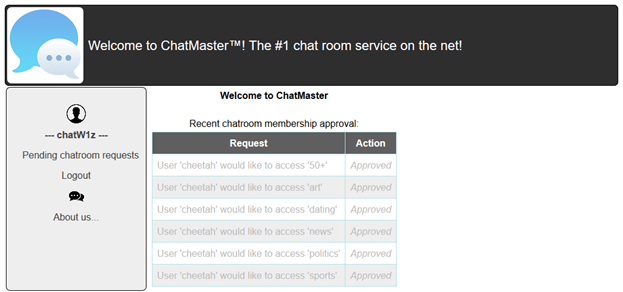
We found how the page gets the chats list and played with the parameters until we got the entire list. Many parameters were useless this is the minimal URL required: http://deceptionisland.xyz/challenge1/chatroomList?utype=0&a=1
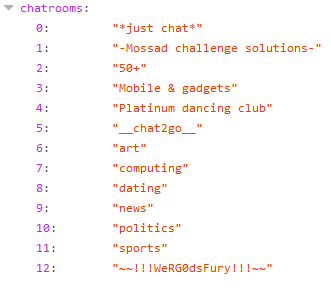
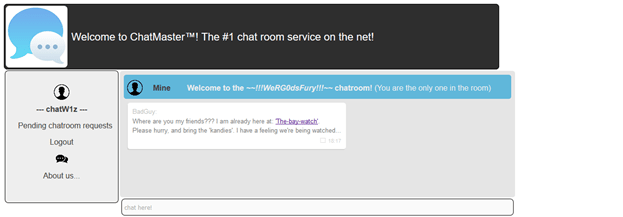
After joining a few chatrooms, we got to ~~!!!WeRG0dsFury!!!~~ chat. Where there was a link to the end.
Hurray.
Challenge 2:

Steganography yay! (ewww)
This is the picture:

Using zsteg we found a string in base64 L2NoYWxsZW5nZTIvYm9tYg== which translates to /challenge2/bomb. Woohoo. Oh no a bomb. Only 3 hours to disarm it.
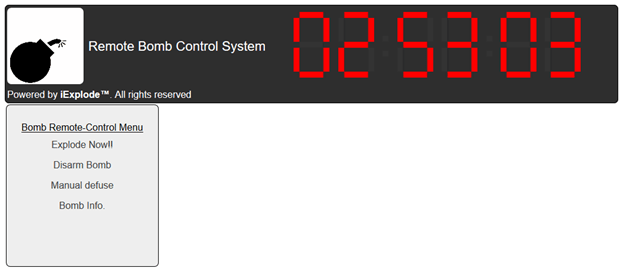
Guess I can't blow it up.
A few more fun pages on the site:
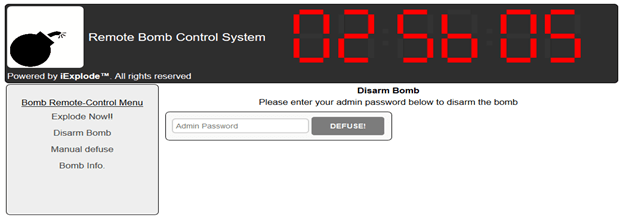
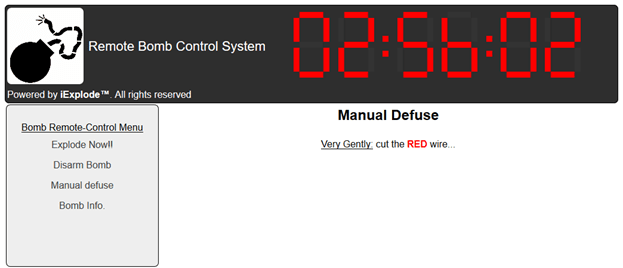
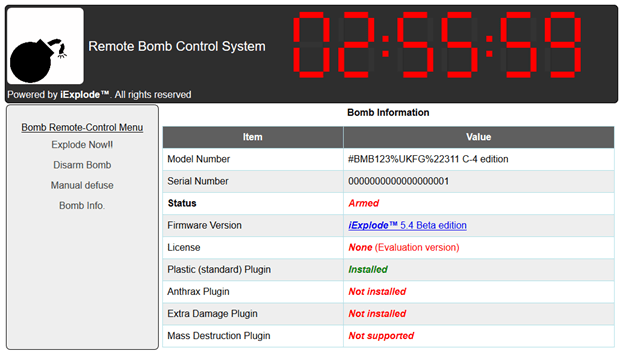
We found some nice pieces of code that led us to the correct password. Basically following the defuse\_page function in \var\www\iexplode.py we found a reference to a function in Pmgmt.pyc after decompiling that it was simple to find the correct password in an array based on the value of another file \etc\iexprun.
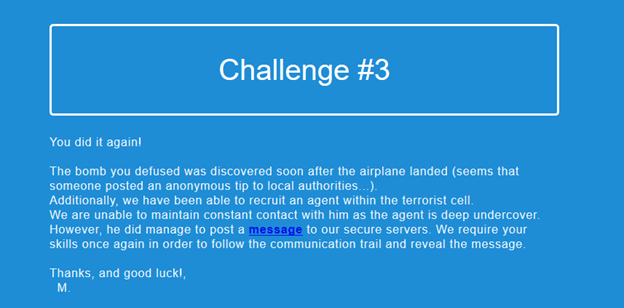
Challenge 3:
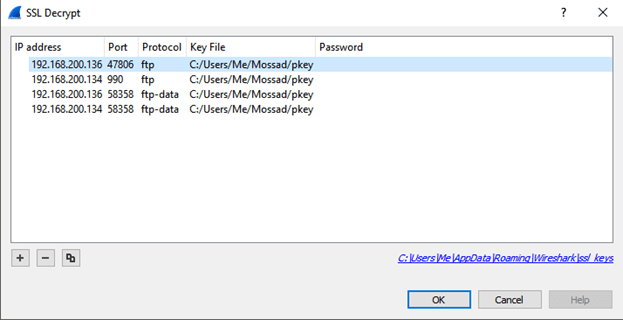
Clicking message downloaded a Wireshark data capture file. In the pcap we found references to two different files, an encrypted private key and a weird text file. We used a password we found to decrypt the private key. We then used the key to decrypt the ssl traffic in Wireshark, along with making sure the passive port was correctly configured to show ftp-data.
The excel file that had a "shopping list", each "price" corresponded to a letter in the weird text file from earlier. Using a simple python script we got a URL. And that's it. Yay!